Technology is rapidly evolving, with robotics, IoT, virtual reality, and augmented reality devices flooding our networks.
Traditional network infrastructures often face significant challenges due to their reliance on manual configurations and command-line interfaces (CLIs) for managing switches, routers, and access points. The outdated designs can be cumbersome and time-consuming, especially as networks grow in size and complexity. Additionally, the reliance on complex protocols like Spanning Tree Protocol (STP) and Protocol Independent Multicast (PIM) can introduce vulnerabilities and increase the operational overhead.
A network fabric is a highly interconnected network topology where every node, including switches and endpoints, is directly connected to every other node. This architecture ensures optimal communication paths, minimal latency, and high availability. Network fabrics are essential for modern IT systems, providing scalability, flexibility, and resilience in data centers and cloud environments. By eliminating single points of failure and enabling efficient load balancing, network fabrics support demanding applications and critical workloads.
Benefits of fabric networks:
- Improved time-to-service: Likely, you’re being asked to deliver more connectivity and enable network changes at an increasing pace. Many of these changes require a maintenance window, thus introducing delays into accommodating the requests. Fabric networking can automate network changes, allowing you to make them in minutes, rather than days or weeks.
- No downtime from human error: Because adding and removing network services in a fabric network only needs to be done at the edge, and is typically done from a centralized management system, mistakes are far less likely and the network is much more stable.
- Better resiliency: Fabric networking provides the opportunity to simplify your network by reducing the number of protocols in use. With a simpler network, recovery times are faster. Also, more interconnectivity means the loss of a link or even a network device will not impact your applications.
- Enhanced security: Fabric networks allow you to easily implement network segmentation with the creation of secure zones. This feature prevents lateral movement across the network. For example, if a system is infected by a virus, the infected system is not allowed to communicate outside of its zone or segment.
- Integrated wired and wireless: With certain fabric technologies you can fully integrate your wired and wireless networks to create a unified campus network. This unification leads to greater simplicity in deploying wireless APs and providing a consistent quality of service across both wired and wireless access.
- Enhanced quality of experience (QoE): Fabric technologies use algorithms to calculate the shortest path between any source and destination. This capability ensures that in any network, users and devices are connected to their applications by the shortest and most efficient path to reduce latency.
Simplifying your network management and automating tasks with Extreme Fabric connect
Extreme Fabric connect relies on Shortest path bridging (SPB) which is an Ethernet-based fabric where all networking services, whether Layer 2, Layer 3, IPv4, IPv6, or multicast, are virtualized and decoupled from the physical infrastructure.
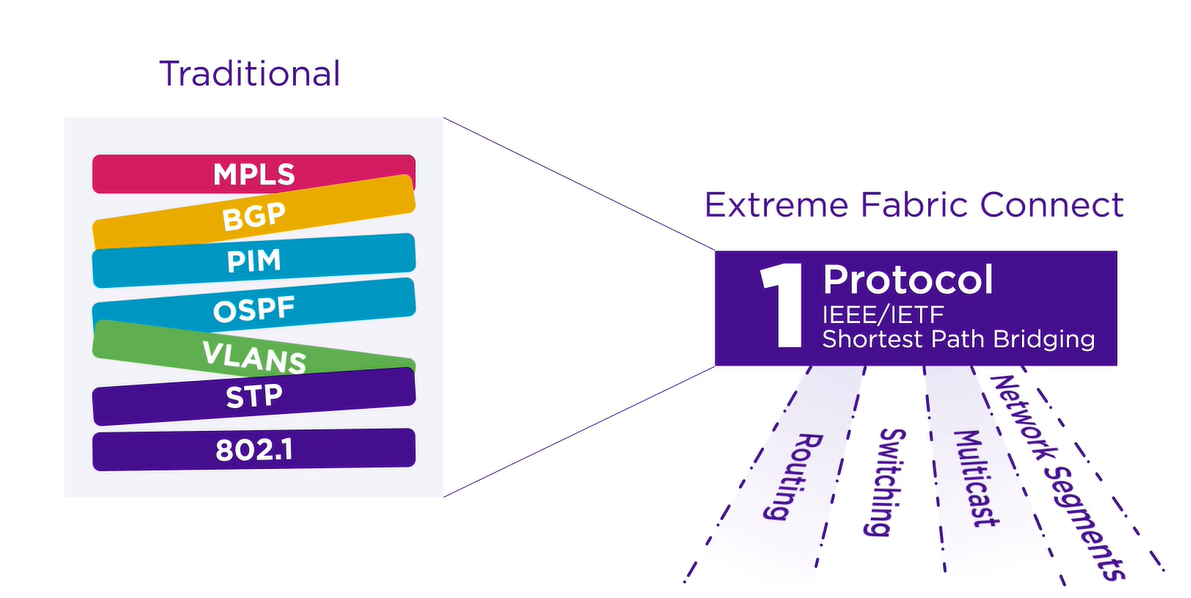
SPB uses Intermediate System to Intermediate System (IS-IS) as the control plane to create a “stateful” network topology. With IS-IS, each switch advertises itself to all other nodes in the fabric area so that each has a complete network topology map. This eliminates the need for traditional layered protocols.
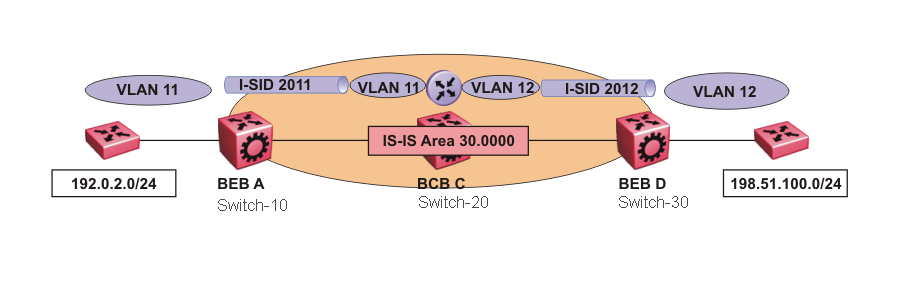
The SPB infrastructure uses VSNs to represent network services, similar to VNIs in IP fabric networks. VSNs can be extended across the network as L2 or L3 VSNs. The simplicity and agility of SPB are due to the ease of extending VSNs, the use of a single protocol, and the clear separation of services from the underlying fabric infrastructure.
Layer 2 virtualized network services (L2 VSNs)
allow you to take Layer 2 VLANs and extend them anywhere in the network — even across geographical distances. These Layer 2 segments can either be E-Line (point-to-point) services, E-Tree (private LAN) services, or E-LAN (any-to-any) services.
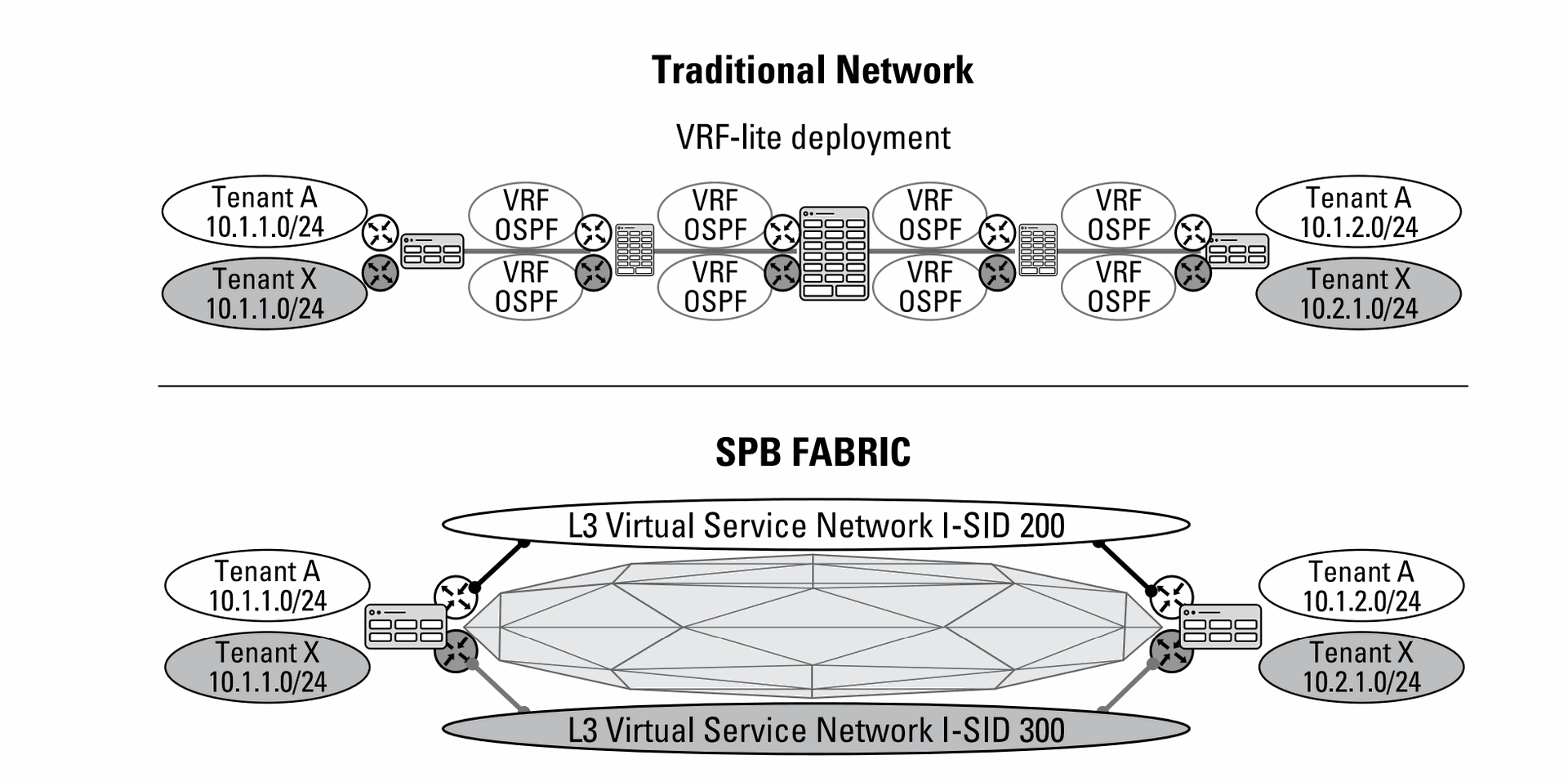
Layer 3 virtualized network services (L3 VSNs)
enable enterprises to separate portions of the network into logical segments, restricting communications to those members of that segment. Layer 3 virtual private networks have their own routing topology, providing a high degree of isolation. They are also scalable and easy to deploy. Layer 3 VSNs are useful in multi-tenant environments as well as environments where IoT devices, applications, user groups, or critical information must be in its own secure segment for security purposes.
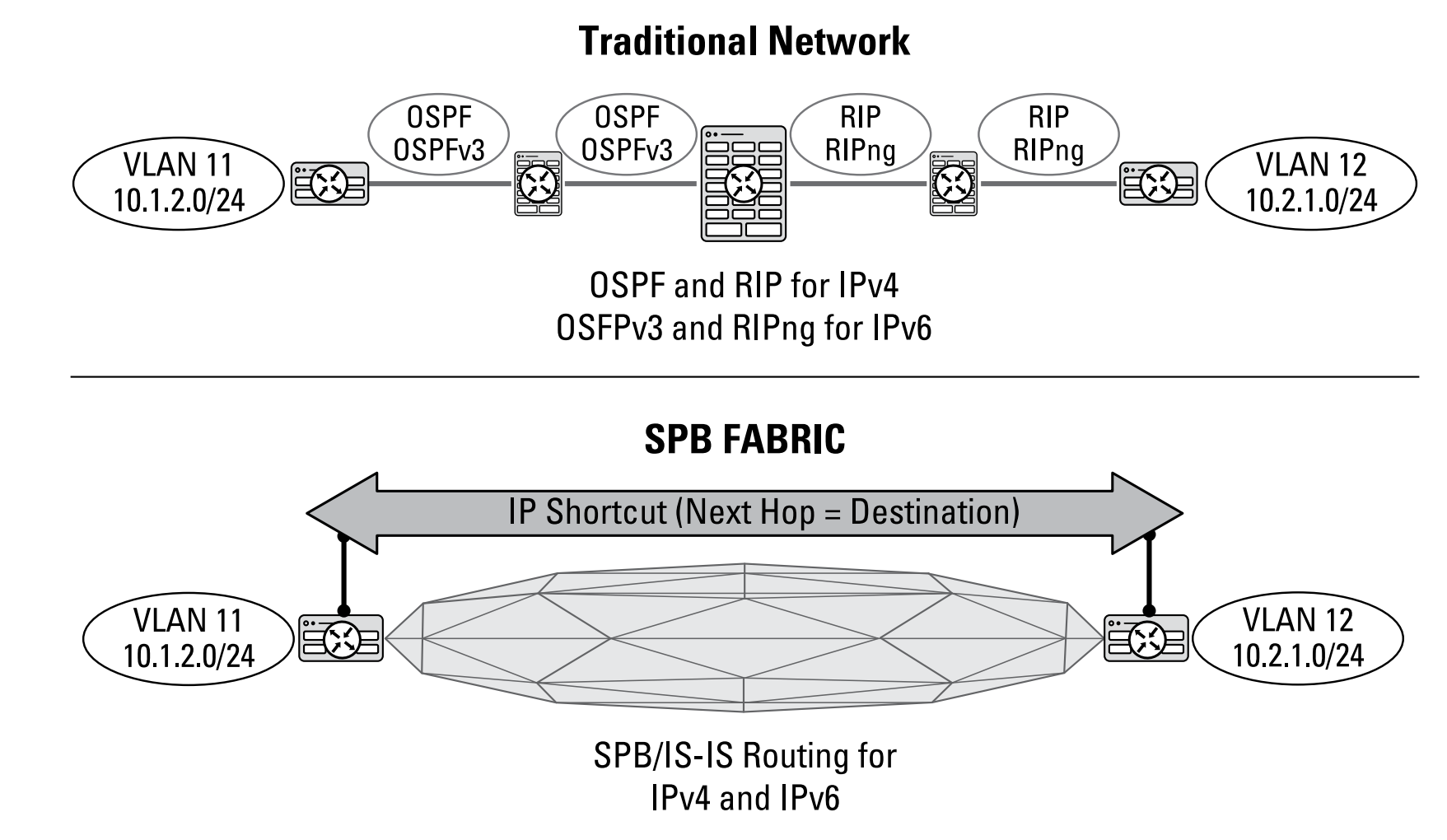
IP shortcuts
leverage the global routing table to forward IP packets directly over the SPB network. Conceptually they are similar to Layer 3 VSNs; however, the difference is that rather than being mapped to an I-SID, the IP encapsulation is mapped directly to an Ethernet header. A route look-up is done on the edge to determine the packet’s destination. The edge node adds the Ethernet header that contains the destination MAC address. The fabric then efficiently cut-through switches to the destination node without any hop-by-hop route look-ups.
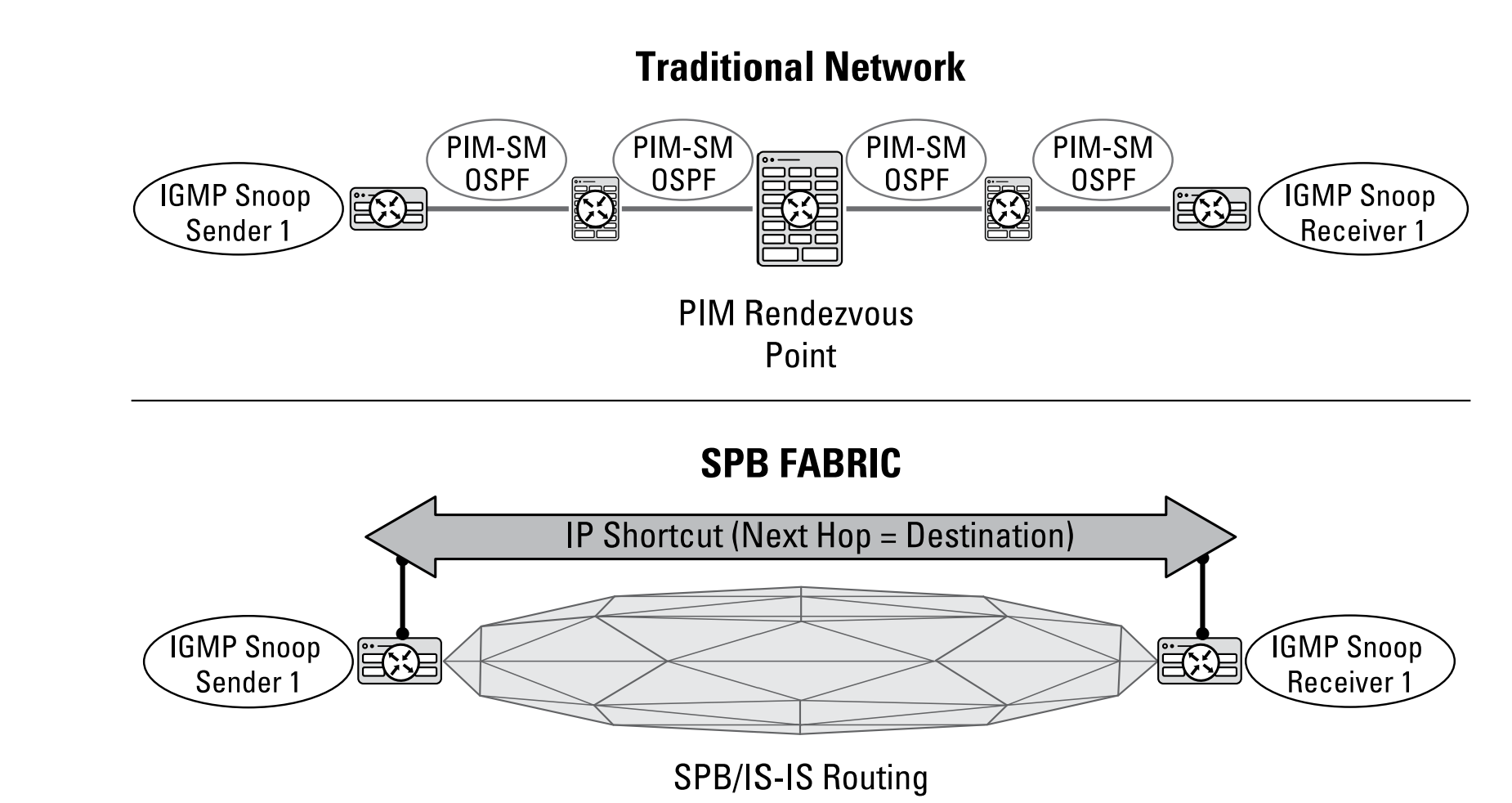
IP multicast
services bring complexity with all the configuration that goes along with setting up Protocol-Independent Multicast (PIM) or Distance Vector Multicast Routing Protocol (DVMRP). With SPB, you don’t have to worry. You get high performance, multicast functionality but without the complex configuration overhead. Multicast over SPB also offers superior performance for any type of multicast deployment whether it is one-to-many (IPTV), many-to-few (video surveillance), or many-to-many. When a multicast stream is received, it is mapped to a dedicated multicast service identifier (or I-SID). IS-IS then advertises the I-SID to the rest of the fabric and forwards it only to nodes that register to receive it through IGMP. If a node does not request the stream, it is not forwarded, enabling far more efficient distribution of multicast traffic than in a traditional network.
Examining the Security Attributes of SPB
One of the biggest challenges with traditional IP network design is that the entire routing table is exposed to every device and every endpoint in the network. This characteristic leads to the ability for a malicious attacker to gain entry to the network, discover the network topology using common IP scanning mechanisms, then move through the network to access your valued data. In an SPB network, this vulnerability is eliminated in many ways:
First, routing is enabled only at the network edges. It doesn’t reside in the network aggregation or core. Rather than forwarding based on IP look-ups, traffic is forwarded using Ethernet switched paths. Therefore, anyone running an IP scan against an SPB environment gets a list of IP subnets all showing just a single hop to the egress of the network. Everything in between is “dark.” This inability to discover the topology of the network makes it nearly impossible for hackers to laterally move to sensitive areas of the network.
Second, the ability to segment the routing tables through Layer 3 VSNs. These secure segments run as ships in the night without any awareness of each other and without allowing any access, in or out, unless otherwise configured. Having a highly segmented environment ensures that if the network is breached, that breach is contained to where it occurred, thus minimizing damage.
Third, eliminating back-door entry points to the network. SPB VSNs can be elastic in nature; they can extend and retract as authenticated users and devices connect to the network and disconnect. When a user disconnects from a switch port and access to the segment is no longer required, residual configuration is automatically deleted on the edge switches. This practice not only removes the delays and risks associated with manually configured conventional networks — it also eliminates the risk of a back-door entry point to the network.
Conclusion
In today's rapidly evolving digital landscape, network infrastructures face increasing demands for scalability, flexibility, and security. Traditional network architectures often struggle to keep pace with these demands, relying on complex protocols and manual configurations.
Extreme Fabric Connect offers a solution to these challenges by simplifying network management and automating tasks. Based on Shortest Path Bridging (SPB), this technology provides a highly interconnected network fabric that ensures optimal communication paths, minimal latency, and high availability.
Related Reference
Fabric Networking For Dummies®.